- Lesson 4: Private, Security and Trust
- Sub-area of data protection in healthcare
- Privacy Consent Models
- Data segmentation
- Models for data segmentation
- Public Key infrastructure (PKI), a solution for Trust
- Interview with Dr. Don Detmer
- Supplementary material
Lesson 4: Private, Security and Trust
People’s Protected Health information ( PHI, healthcare data that is linked to information that identifies the patient) is protected by HIPPA. PHI can only be accessed by authorized person for legitimate purpose.
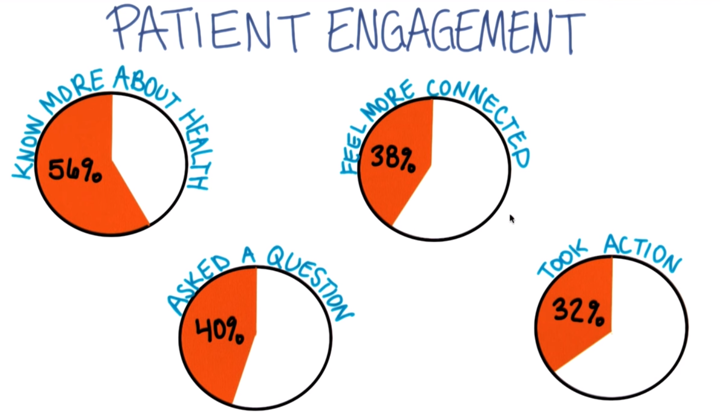
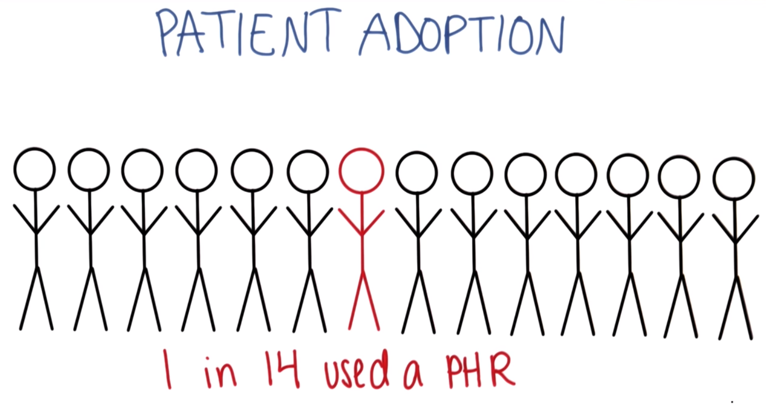

And most of people do not even want their data to be digitized.
Sub-area of data protection in healthcare
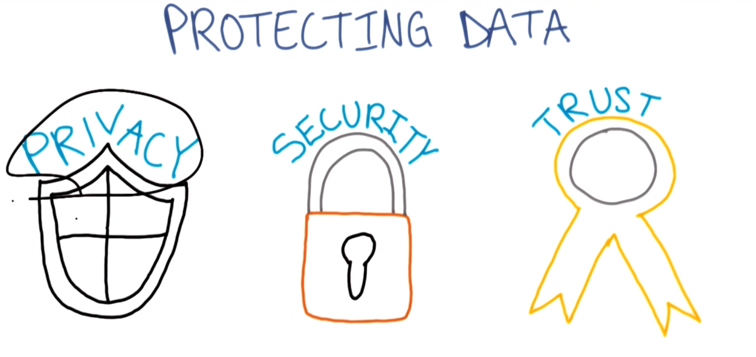
- Privacy: only people authorized by patient can see health data.
- Security: data is protected from unauthorized access.
- Trust: senders and recipients of health information knows that the people they are interacting with are who they say they are.



Privacy Consent Models

CurrentCare uses Opt-in model.
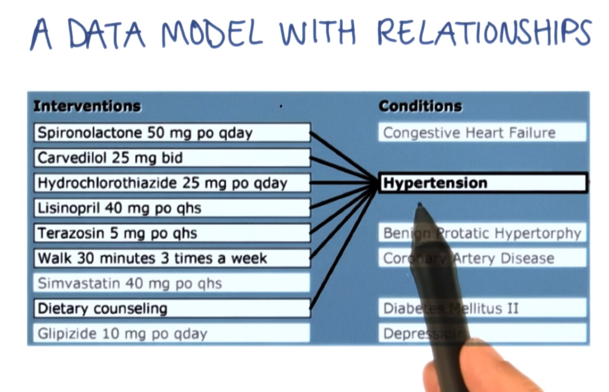
Data segmentation
Models for data segmentation

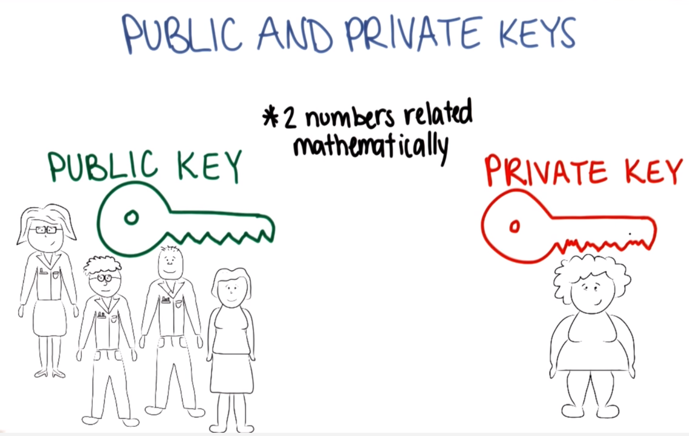
Public Key infrastructure (PKI), a solution for Trust

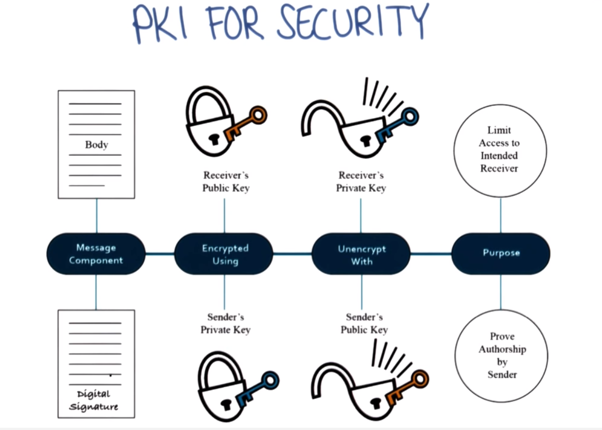


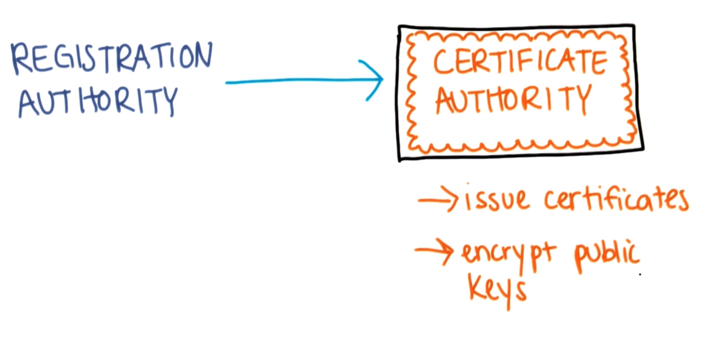
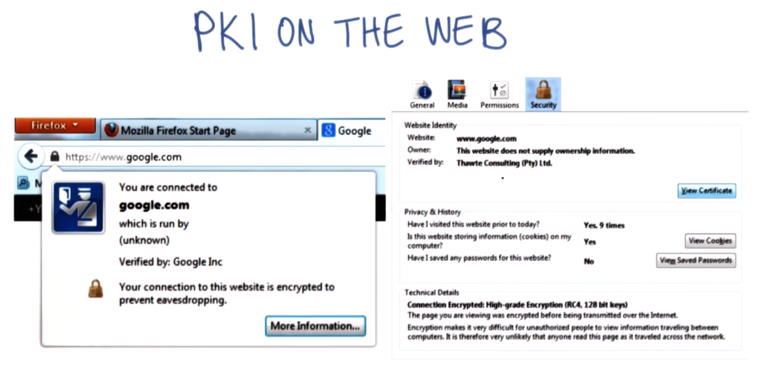
Interview with Dr. Don Detmer
Q1. Where we are in transforming our healthcare systems with HIT, and what’s the future?
A: digital records were believed to be essential in healthcare in 1991, but it is in 2009 when HITECH legislation started, things becomes more exciting. Current HIT is in developing, there are things that are exciting and things we don’t like. The use of HIT in terms of computer technology and communication technology are very exciting right now.
Q2. getting digital health data is import but time consuming, the concern is the patients’ privacy issues. Does the emphasis of privacy harming the use of data, how to balance privacy and data sharing?
A: HIPPA is developed pre web area with the paper system in mind. Misuse of the data at that time can bring real harm to people and to the society. But researchers and students want to use the data for research and educational purpose which usually have very low risk. Patients like the idea of using big data for research but culturally they might now want to share their data. We really need very big dataset to address the new health problems. Because of the privacy issue, a lot of study could not even get started. Data liquidity (relative free flowing of data) is an important issue the field needs to solve.
Q3. What’s your thought on Patient generated and controlled data repository (VIA PHR), will it contribute to the share of clinical data for research and other purpose.
A: It sounds great but researchers might ended up getting disportionately represented data because certain group of the population decide to opt out.
Supplementary material
064/100 《Contemporary Health Informatics》Chapter 4 Summary
Key Concepts/Vocabulary
● HIPAA ● Protected Health Information (PHI) ● De-identified health information ● Privacy ● Security ● Trust ● Personal Health Records (PHRs) ● Privacy Consent Models ● Data Segmentation ● Data Segmentation Models ● Public Key Infrastructure (PKI) ● Public and Private Keys ● Registration Authority ● Certificate Authority
Readings
- California Health Foundation patient survey
- Xerox comments on the results of their online survey
- Decision Support for Data Segmentation (DS2)
- RSA Code Made Easy
- A Robust Health Data Infrastructure
- The De-identification Standard
- The Computer-Based Patient Record: An Essential Technology for Healthcare
Graphics
Websites
- ONC’s Standards and Interoperability Framework’s home page
- S&I Framework Wiki
- DS2 Project Home Page
- The NORC X-ID System
2015-09-07 初稿
2015-09-08 添加 Interview with Dr. Don Detmer 部分